DEEP Conference
We recognized the need to address information security at all levels at the same time and the same place.
We value the importance of knowledge and experience sharing.
Therefore, we provide everyone with the opportunity to share their knowledge and build their new experiences. Dive in and go deep with us.
- Why go deep with us?
- Learn from experts and share your knowledge and ideas
- Share global and local trends
- Network
- Choose topics and tracks by yourself
- Initiate new projects and collaborations
- Who should go deep with us?
- Those who manage corporate and information security
- Folks from the IT and IT security
- Penetration testers
- SOC members from all levels

Drill down to the bit level
Technical and low level stuff is in the focus here. It might be a game for some, but various real-world attack simulations can be expected in here, as well as hacking, exploits and malware dissecting. New ideas on how to identify and exploit vulnerabilities are more than welcome.

Organize your protection!
A combination of technical and management stuff is in the focus here. How to orchestrate people, technology and processes to achieve maximum protection efficiency? Topics such as infrastructure protection, damage control, threat intelligence and incident response. Case studies can be found in this track.

Manage the risks, protect your business!
It’s all about management in here; governance, risk, compliance and business in general. Most of the people in here will try to get everyone on the same high-level page. It’s about understanding each other and dealing with future ideas and collaboration between business areas.






Find out in this video!
DEEP Conference
DEEP Conference

in Diverto d.o.o.

at Budapest University of Technology and Economics




Technical Account Manager at NETSCOUT

at Graz University of Technology

for Adriatics & Hungary at Thales

at Rimac automobili

at Celsius

at Končar KET

at A.P. Moller – Maersk





in Diverto d.o.o.

in Technical Leader for Cisco Talos.



how to become part of it?


Workshop: The Situation Room
by Bojan Alikavazović
Do you want to test your decision-making abilities to see how well you manage crisis situations? This room will provide a unique educational opportunity that will guide you through key moments in a cyber incident on critical infrastructure. Whether you are from a technical or management world this workshop is the place to be! We are not looking for your technical skills, but decision-making skills!
Bojan Alikavazović is a senior consultant for information security in Diverto d.o.o. He is a member of Security Operation Center (SOC), responsible for monitoring, processing and managing security incidents in different business environments. He is experienced in penetration tests, reverse engineering of the malicious code, security hardening, revision of network architecture for the security improvement, as well as in integrating various solutions for detection and blocking of cyber-attacks.
Workshop: Capture the Flag
by Filip Rapaić
Capture the Flag (CTF) is a competition where the entrants are solving different tasks from the fields of information technology and information security. The tasks are usually interesting and educative, requiring from the entrants to find certain parts of the text, called the flag. It might be hidden on a server, at a page or wherever an information could be hidden. CTF is open for all, there are no pre-requirements for entering it, so there is no reason why you shouldn’t try to participate, even in anonymous mode. It is also worth to participate knowing that the best entrant can earn some valuable prizes.
Filip Rapaić is an information security consultant in Diverto d.o.o. He is a member of the Security Operation Center (SOC), an entity responsible for monitoring, processing and handling the security incidents in various business environments. His fields of expertise are the incident responding and malicious code analysis. At Diverto he is also a specialist for Capture the Flag (CTF).
ML Security Evasion Competition 2020
by Zoltan Balazs | .ops
Research attacking ML-based image classifiers is common, but it is less frequent to see a study on how someone can bypass ML-based malware detection. Authors of presentation are Zoltan Balazs and Hyrum Anderson.
In 2019, they organized a contest where participants had to modify Windows malware in a way where the provided three ML engines do not detect it. However, the modified sample is still functionally equivalent to the original binary. As it turned out, it is not that hard to come up with a generic solution which can bypass all three engines. In this presentation, we will discuss the details of the contests from 2020 and 2019, some of the techniques used by the participants (packing, overlays, adding sections), and information on the defensive tracks.
Zoltan Balazs (@zh4ck) is the Head of Vulnerability Research Lab at CUJO AI, a company focusing on smart home security. Before joining CUJO AI he worked as a CTO for an AV Tester company, as an IT Security expert in the financial industry for five years, and as a senior IT security consultant at one of the Big Four companies for two years. His primary areas of expertise are penetration testing, malware analysis, computer forensics and security monitoring. He released the Zombie Browser Tool that has POC malicious browser extensions for Firefox, Chrome and Safari. He is also the developer of the Hardware Firewall Bypass Kernel Driver (HWFWBypass), the Encrypted Browser Exploit Delivery tool (#IRONSQUIRREL) and the Sandbox tester tool to test Malware Analysis Sandboxes.
He found and disclosed a vulnerability in IP cameras, and this vulnerability was exploited by the Persirai botnet, running on ˜600 000 cameras.
He has been invited to give presentations at information security conferences worldwide including DEF CON, SyScan360, SAS2018, Virusbulletin, Disobey, Deepsec, Hacker Halted USA, Botconf, AusCERT, Nullcon, Hackcon, Shakacon, OHM, Nopcon, Hacktivity, and Ethical Hacking.
Implementation of PAM solution in Fina
by Ivan Poljak | .ops
An analysis of how the PAM solution was implemented in Fina system, presented by one of the key people who were involved in that process. Case study of PAM implementation in an extremely complex environment with huge number of systems and different access levels.
Ivan Poljak is one of the leading Fina engineers for cyber and IT security. He was involved in setting up of different security solutions (SIEM, DAM, APT, DLP, PAM) and actively contributes to ongoing development of different services within Fina, due to his vast experience. He graduated at FER and works at Fina since 2008., as system architect, security administrator, security analyst and security team leader at diverse Fina projects. He is actively involved in CERT’s work on recognition and blocking of security threats within FINA.
IT vs. OT: We are Much More Similar than We are Different - Comparing Process Control Room and SOC Operations
by Marina Krotofil | .lead
Critical infrastructure protection has been a high-profile topic for at least a decade. One reason for this is the growing exposure of industrial environments to security threats through the use of the Internet as well as through the use of standard hardware and software, from which they were historically isolated. Another reason is that the potential impact of attacks on critical infrastructures can no longer be ignored. In the past years, IT security experts became increasingly more involved with the protection of industrial control systems against cyber-threats and becoming responsible for establishing consolidated IT-OT SOCs. However, the harmonization of modern IT security approaches and the traditional process control culture is far from reality. The purpose of this presentation is to help IT security experts understand the specifics of OT environments as well as the associated vocabulary and mindset.
Using the example of monitoring functions of IT infrastructures and industrial processes, as well as two seemingly very different job functions such as SOC Analyst (IT) and Control Room Operator (OT), it will be shown that the operational tasks of both job functions are fundamentally very similar. During the presentation, the similarities and specifics will be discussed in the context of key areas such as vocabulary, types of anomalies/events/threats, SIEM vs. HMI applications, alarm configuration and management, anomaly detection, event logging, and SOPs. Additionally, on the example of a real security incident, it will be shown how IT and OT teams can interact and work better together.
After this presentation, IT security experts will have a much better understanding of daily OT operations and its ecosystem, understand IT-OT synergies, and identify opportunities for cross-functional learning. But more importantly, IT experts will be able to better communicate with OT colleagues and ultimately achieve the much discussed "IT-OT Convergence".
Marina Krotofil is a Cyber Security Product Owner, Industrial Technologies: Connected Vessels, Terminals and Warehouses at A.P. Moller – Maersk in UK, with a decade of experiences in advanced methods for securing Industrial Control Systems (ICS). She is also an experienced Red/Blue Teamer who contributed research on novel attack vectors and advanced exploitation techniques, incident response, forensic investigations and ICS malware analysis. Previously, Marina worked as a Cyber Security Lead at ABB (UK), Senior Security Engineer at BASF (Germany), Principal Analyst and Subject Matter Expert (SME) in the Cyber-Physical Security Group at FireEye (USA), Lead Cyber Security Researcher at Honeywell (USA) and a Senior Security Consultant at the European Network for Cyber Security (Netherlands). She authored more than 25 academic articles and book chapters on ICS Security and is a regular speaker at the leading conference stages worldwide. She is also a frequent reviewer of academic manuscripts and talk proposals including Black Hat and USENIX WOOT. Marina holds an MBA in Technology Management, MSc in Telecommunications, and MSc in Information and Communication Systems.
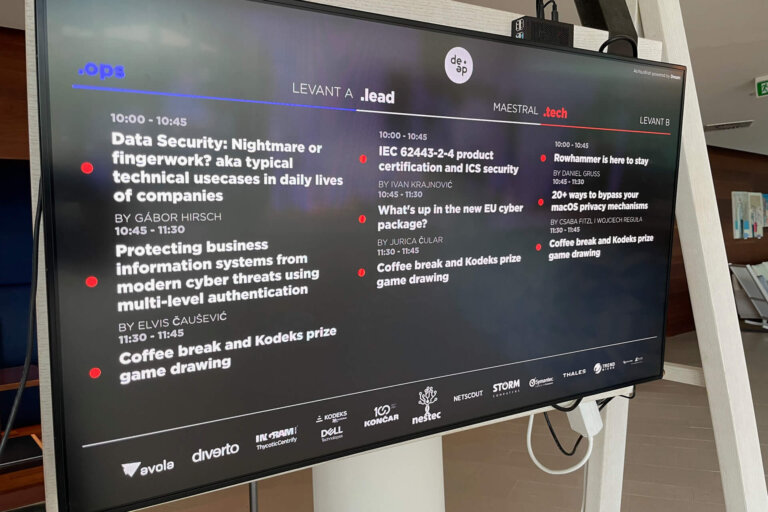
Data Security: Nightmare or fingerwork? aka typical technical usecases in daily lives of companies
by Gabor Hirsch | .ops
With the entry into force of the GDPR, data protection is becoming increasingly important and emphasized in the lives and daily lives of companies. Thanks to diversified IT architectures, it is becoming increasingly difficult to comply with strict compliances. In the presentation, Gábor will review the typical usecases that a company faces on a daily basis and also offer a possible solution to the problems that arise.
Gábor Hirsch graduated at Bánki Donát Technical Collage as information technology engineer and teacher. In the last 20 years he held on a lot of manager positions in information security and network security companies. Among others he established and lead the Check Point distribution and IT security business unit in DNS Hungary (today is Arrow ECS) and as business development manager of Cisco Hungary he responsible on the success of the Cisco security products. He was the first employee of Fortinet in Hungary and built the channel, brand and the team. Parallel his business carrier he took part in professional activities: he was member of Check Point Advisory Council, from 2008 till 2018 he was the leader of the information and IT security workgroup at IT Association of Hungary, and he was associate lecturer of King Sigismund University (today Milton Friedman University) and University of Public Service. Before he joined to Thales as Regional Sales Manager he managed several data security and information security projects as independent advisor, worked as DPO and collaborated GDPR related projects in other advisories like PriceWaterhousCoopers.
IEC 62443-2-4 product certification and ICS security
by Ivan Krajnović | .lead
In recent years the industrial control system standard landscape in Europe has focused on two key standards - IEC 62443 and IEC 62351.The IEC 62443 standard defines procedures, roles, responsibilities and high-level technical requirements for operators, integrators, developers, etc... The IEC 62351 standard defines the technical details - security architecture, end-to-end encrypted versions of various telecontrol protocols, syslog and snmp security logging reporting, RBAC, key management etc... The presentation talks about Končar-KET experiences obtaining IEC 62443-2-4 certification for two of their SCADA products, reviews other similar standards and reflects on the general practices and state of security in ICS systems.
Ivan is a principal software architect at Končar-KET, specializing in industrial automation and control, mathematical process modelling, distributed systems and IT/OT convergence. His code runs the key control components of some 300+ electrical transformer stations, power plants, control centres and other industrial sites with years of continued uptime. As a key cyber security expert and developer, he is a member of IEC TC57 WG15 group, dealing with data and communication security and IEC 62351 standard, and WG13/14 groups dealing with electrical grid information modelling and exchange (CIM). Ivan Krajnović received his master’s degree in computer science from the University of Zagreb.
Three million new jobs and how to become part of it? | .lead
Can Croatia be competitive in information security knowledge and experience needed for a booming industry? More than three million new jobs in that sector are expected to be created within next few years. An interesting subject will be discussed by head of postgraduate specialits study Information Systems Security Management and Auditing at Faculty of Organization and Informatics Assoc. Prof. Renata Mekovec, Ph. D., mr.sc. Marinko Žagar, head of Laboratory for information security and privacy at Faculty of Electrical Engineering and Computing doc. dr. sc. Stjepan Groš, as well as our experts, Marko Grbić from Avola and Alen Delić from SpotMe.
All about locks - a neglected side of security (powered by Perger)
Known in the world under the pseudonym" Lockpicking ", this is a demonstration of the physical protection of spaces and buildings where the weaknesses of various locks and similar locking equipment are easily visible and displayed. The DEEP participants will have the opportunity to try opening the locks of various security standards with the support of Mateo Benceković from the Lock opening craft "Perger" and will be able to clearly see the weaknesses of the locks and their protection. The aim of this part of the conference is to raise awareness of the need to protecting the physical space from the perspective of information security and beyond the scope of procedures, processes and protections of IT systems alone.
Information security lessons from banks and crypto realm | .lead
Which information security practices are applied in traditional financial institutions and in decentralized crypto platforms, what are fundamental differences between them and how information security is achieved? At Deep conference we'll talk about this with Alberto Gusella, Chief Security Officer at ZABA and with Shiran Kleiderman, Chief Security Officer & Head of IT at Celsius. Discussion will be moderated by Ivan Kalinić from Diverto. Don't miss this one!
Efficient Detection of Malware on Embedded IoT Devices
by Dr. Boldizsár Bencsáth | .tech
After IoT devices started to spread out throughout the internet, malware-based abuses of those devices are on the rise.
From our malware repository we copied 150,000 samples of IoT related malware for analysis. We obtained initial analysis results (how A/V software classified them) and analysed them to have similarity information. These initial steps let us have a first classification of the samples, resulting plausible classes of similar samples. We started to analyse samples both automatically and manually and found some interesting insights. For example, some malware samples built on the leaked source code contained symbol information, and that helps us a lot to identify functions in malware samples that do not have such symbol information incorporated. Also, we can investigate evolution of some functionality by looking up the code parts in the evolution of the samples.
Ultimately, scaling of code level analysis of IoT malware samples is something possible and can help us to better detection and better understanding of the situation. In addition to the previous topic, I will try to give some insight about installing emulation-based environment, a "sandbox", for which we already see malware samples to build detection and anti-analysis efforts.
I will shortly talk about building such sandbox environments and how to avoid malware to circumvent analysis in the environment.
Dr. Boldizsár Bencsáth received the M.Sc. and Ph.D. degrees in Computer Science from the Budapest University of Technology and Economics (BME) in 2000 and 2009, respectively. He also earned the M.Sc. degree in economics from the Budapest University of Economics. From 1999, he is member of the Laboratory of Cryptography and Systems Security (CrySyS) of BME. His research interests are in network security, including DoS attacks, spam, malware, botnets, and cyber-physical system security.
Among other things, Boldizsár also works in multiple start-up companies of the lab and participates in a number of consulting projects in the field of ethical hacking, security design and forensics. Boldizsár led the team in the CrySyS lab that investigated the Duqu malware and later worked on a number of other well-known APT attacks and currently works on actual questions of malware-based attacks, cyber-physical system security (including cars, factories, nuclear power plants), and other related topics.
Friend or enemy? - hunting for dual usage tools | .tech
It's difficult to read any information security news lately without learning about large corporations being extorted by cyber criminals. In today's threat landscape, organisations increasingly rely on red teams to identify risks and mitigate vulnerabilities in their infrastructure, so much so that an entire industry exists around tools to help facilitate this effectively and efficiently as possible.
Dual-use tools are developed to assist administrators in managing their systems or assist during security testing or red-teaming activities. Unfortunately, many of these same tools are often co-opted by threat actors attempting to compromise systems, attack networks, or otherwise adversely affect companies. This talk discusses the topic of dual-use tools and how they have historically been used in various attacks. We dig deeper in dual-use tools detection to try to find out who could hide behind them - a friendly red team member or a real attacker?
Vanja Švajcer works as a Technical Leader for Cisco Talos. He is a security researcher with more than 20 years of experience in malware research and detection development. Prior to joining Talos, Vanja worked as a Principal researcher for SophosLabs and led a Security Research Team at Hewlett Packard Enterprise.
Vanja enjoys tinkering with automated analysis systems, reversing binaries and analysing mobile malware. He thinks time spent scraping telemetry data to find indicators of new attacks is well worth the effort. He presented his work at conferences such as Virus Bulletin, RSA, CARO, AVAR and many others.
Rowhammer is here to stay
by Daniel Gruss | .tech
The Rowhammer effect was known for multiple decades but only got widespread attention around 6 years ago when its security implications were observed for the first time. In this talk, we will discuss various attacks and mitigations that have appeared in a cat-and-mouse game over the past years. However, on recent off-the-shelf systems the Rowhammer effect is still relevant. We will discuss why the Rowhammer effect is not yet successfully mitigated and still will not be when academic mitigations reach practice. Finally, we will show what the fundamental misunderstandings in our community are that lead to the repeated revival of the Rowhammer effect.
Daniel Gruss (@lavados) is an Assistant Professor at Graz University of Technology and will be one of the presenters at DEEP .tech track. He finished his PhD with distinction in less than three years. He has been involved in teaching operating system undergraduate courses since 2010. Daniel's research focuses on side channels and security on the hardware-software boundary. His research team was involved in several vulnerability disclosures, including Meltdown and Spectre. He has co-authored more than 20 top-tier academic publications in the past five years and received several prizes for his research.
ATT&CK or !ATT&CK that is the question
by Robert Petrunić| .ops
This presentation is addressing some of really important questions in our business.
What is it about and is it significant for you? Let’s check:
Do you use MITRE ATT&CK framework?
If you are a red teamer, blue teamer or incident handler - you should. To make it simpler, if you are an X teamer - you should definitely use it. If you are an adversary - you probably already are using it.
So, what's the point behind it?
Released to the public in 2015, MITRE ATT&CK framework gives the context to the attack. Instead of trying to identify tools and malware used in adversary campaigns, the focus is on techniques (how) and tactics (why). If you want to learn about MITRE ATT&CK framework and how to use it in your incident handling or X teaming - this is the right lecture for you. Or, if you just want to see the process a decent hacker would go through (DEMO: from initial foothold to persistence), you should join us too.
Of course, Robert will do the talk on the basis of vast personal experience. He works as a senior information security consultant in Eduron IS, the company dedicated to IT security education, penetration testing and computer forensics. He is also a lecturer in most successful Croatian private college Algebra - university college for applied computer engineering, where he has designed several courses related to computer security and forensics.
Robert is Microsoft certified trainer since 2002, EC-Council certified trainer since 2008 and ISC2 certified trainer since 2014. He works mainly in security field starting 2004, and Microsoft acknowledged this at 2008, assigning him Microsoft most valuable professional recognition for nine years in a row. For the last sixteen years Robert is working on programs related to ethical hacking and IT security awareness for systems administrators, developers and IT security consultant. He is also often a lecturer at regional IT conferences.
Breaking authentication and authorization on major OAuth2 providers
by Josip Franjković | .tech
The security of OAuth2 providers has increased tremendously over the past several years, however some common (and uncommon) pitfalls still remain. This presentation will, as part of our red track, showcase a collection of vulnerabilities, including account takeovers with no interaction needed, cross-site request forgery vulnerabilities allowing account control, authorization issues with high or critical impact, and other miscellaneous bugs in some of the world's largest companies. All of the examples are fixed, and will have a root cause analysis, proof-of-concept steps, how companies like Facebook, Microsoft and Paypal approached fixing these issues, and how you can avoid these bugs as either the provider or a client.
Josip Franjković is a freelance security researcher and a "bug bounty hunter". Throughout his career he has reported over 200 verified vulnerabilities to companies like Facebook, Google, Microsoft, PayPal, Yahoo and others, with a main focus on authentication and authorization vulnerabilities.
Josip is a Diamond league HackerPlus member on Facebook, and tops their whitehat list in the '17-'19 period. He has also participated in live hacking events around the world for PayPal, Yahoo and Facebook, where he was asked to find vulnerabilities in yet to be released software and hardware, winning one of them and placing among the top three participants multiple times.
New methods of security printing in the infrared and visual spectrum
by Dr. Jana Žiljak Gršić I.tech | .ops
Jana Žiljak Gršić will present a new method of security printing of highly protected data. She is one of the authors of the Infrared design patent, which is a revolutionary technological solution for security data printing processes. The innovation refers to the application of the infrared effect in printing technology with the aim of preventing counterfeiting. The solution enables secure printing of data in two spectral regions; visual and infrared. It determines the generation of colour with completely different behaviour in areas affected by IR light. IR label detection is only possible with instruments that "see" at wavelengths above 700 nm and that can convert IR graphics into an object/image visible to the human eye. By using specific features that come from programming capabilities for digital and conventional printing, the algorithms are derived by including two or more colours that are the same colour (in daylight) but with completely different behaviour in IR light. The same image is separated by a dual algorithm, depending on the target visibility or invisibility in IR light. The modification of certain graphics protections is programmed, first for one and then another combination. The contribution is in the field of security for all data that are printed such as code, images on documents and securities, product traceability labels, as well as for archived files. She participated in numerous scientific researches in the field of graphic security, is the winner of the State Award for Science for 2010 for exceptional contribution to the development of science, and is an associate member of the Croatian Academy of Engineering. She is a permanent forensic expert for graphic technology, design, manuscripts, documents, securities, money, paintings, credit, and other cards. She is employed at TVZ and the University North. She teaches the study of Information Security and Digital Forensics at TVZ.
What's up in the new EU cyber package?
by Jurica Čular | .lead
In December, 2020, European Commission and the High Representative of the Union for Foreign Affairs and Security Policy presented a new EU Cybersecurity Strategy. As a key component of Shaping Europe's Digital Future, the Recovery Plan for Europe and the EU Security Union Strategy, the Strategy will bolster Europe's collective resilience against cyber threats and help to ensure that all citizens and businesses can fully benefit from trustworthy and reliable services and digital tools. This lecture brings insights to new strategic and legislative document brought by the new cyber package.
Jurica Čular graduated at Faculty of electronics and computer science, Zagreb, Croatia as Master of Computer Science. Got an MBA in finance and marketing at Kelley School of Business, Indiana University. Holds several information security certificates like CISA, CISSP, ISO 27001 LA. Worked as an information security consultant for financial institutions and Big 4. Spent 9 years working as an expert advisor in Information Systems Security Bureau. Currently working as a Security Governance Expert in Infobip ltd.
Taming the tiger: From startup to Enterprise
by Dubravko Hlede | .ops
Adapting IT security for fast growing company while enabling user creativity is not without its challenges. Having to tackle threats like Identity theft, Ransomware, GDPR, Data theft, BEC, C-Level Fraud, Remote work was fun. Now we created world fastest car and acquired Bugatti, target on our back just got a lot bigger.
Here you will see couple of ways to protect complex IT systems using available tools and services.
Dubravko Hlede is IT operations manager in Rimac automobili for almost 5 years. Before that he was team lead/IT manager/Director of IT in various industries, such as finance, automotive, wholesale and retail. His experience among others includes developing systems for R&D of Autonomous driving, advance simulation environments for thermal dynamics and crash testing. In 17 years of experience he acquired numerous certificates form Microsoft, Cisco, IBM and AWS.
Best practices for DDoS mitigation in modern enterprise networks
by Marco Gioanola | .tech
During this session we will look at the latest trends of DDoS attacks and evolutions of enterprise network infrastructure. We will highlight the most important factors that companies need to consider when building secure and resilient networks. We will specifically discuss the challenges related to the adoption of cloud services and encrypted protocols.
Marco Gioanola has designed DDoS mitigation services for Internet Service Providers and Enterprises for more than 15 years with Arbor Networks, now part of NETSCOUT. He has worked for four years as service architect for Arbor Cloud, the largest purpose-built DDoS mitigation network globally. Previously to joining Arbor he participated in the startup of a Managed Security Services company and managed projects related to cryptography and Certificate Authorities for banking customers.
Fuzzing the macOS kernel
by Antonio Zekić | .tech
Antonio Zekić is a senior information security consultant in Diverto d.o.o. He is experienced in penetration testing and reverse engineering. In spare time he enjoys fuzzing, exploit writing with an emphasis on iOS/macOS vulnerability research. He is a regular speaker at the security events in the region.
Antonio's lecture 'Fuzzing the macOS kernel' will provide a general introduction to vulnerability analysis, fuzzer development process as well as fuzzing techniques and the macOS kernel debugging.
20+ ways to bypass your macOS privacy mechanisms
by Csaba Fitzl and Wojciech Reguła | .tech
"TotallyNotAVirus.app" would like to access the camera and spy on you. To protect your privacy, Apple introduced Transparency, Consent, and Control (TCC) framework that restricts access to sensitive personal resources: documents, camera, microphone, emails, and more. Granting such access requires authorization, and the mechanism's main design concern was clear user consent.
In this talk we will share multiple techniques that allowed us to bypass this prompt, and as a malicious application get access to protected resources without any additional privileges or user's consent. Together, we submitted over 40 vulnerabilities just to Apple through the past year, which allowed us to bypass some parts or the entire TCC. We also found numerous vulnerabilities in third-party apps (including Firefox, Signal, and others), which allowed us to avoid the OS restrictions by leveraging the targeted apps' privileges.
In the first part of the talk, we will give you an overview of the TCC framework, its building blocks, and how it limits application access to private data. We will explore the various databases it uses and discuss the difference between user consent and user intent.
Next, we will go through various techniques and specific vulnerabilities that we used to bypass TCC. We will cover how we can use techniques like process injection, mounting, application behavior, or simple file searches to find vulnerabilities and gain access to the protected resources.
The audience will leave with a solid understanding of the macOS privacy restrictions framework (TCC) and its weaknesses. We believe there is a need to raise awareness on why OS protections are not 100% effective, and in the end, users have to be careful with installing software on their machines. Moreover - as we're going to publish several exploits - red teams will also benefit the talk.
Csaba Fitzl graduated in 2006 as a computer engineer. He worked for 6 years as a network engineer, troubleshooting and designing big networks. After that, he worked for 8 years as a blue and red teamer focusing on network forensics, malware analysis, adversary simulation, and defense bypasses. Currently, he is working as a content developer at Offensive Security. He gave talks/workshops at various international IT security conferences, including Hacktivity, hack.lu, Troopers, SecurityFest, DEFCON, and Objective By The Sea. Csaba spends his free time with his family, practices ashtanga yoga before sunrise, or hikes in the mountains.
Wojciech Reguła is a Principal IT Security Specialist working at SecuRing. He specializes in application security on Apple devices. He created the iOS Security Suite - an opensource anti-tampering framework, Bugcrowd MVP, found vulnerabilities in Apple, Facebook, Malwarebytes, Slack, Atlassian, and others. In his free time, he runs an infosec blog - https://wojciechregula.blog and shared research on among others Objective by the Sea (Hawaii, USA), AppSec Global (Tel Aviv, Israel), AppSec EU (London, United Kingdom), CONFidence (Cracow, Poland) and BSides (Warsaw, Poland).
Protecting business information systems from modern cyber threats using multi-level authentication
by Elvis Čaušević | .ops
User data, which most often contains a username and password, as well as the use of passwords with a small number of characters that are easy to guess through various tools, are today the most common target of cyberattacks. Such attacks jeopardize access to and theft of both private and business data. The consequences of data loss are large and expensive, and as an additional problem, there is the impact of a bad reputation that the market is beginning to monitor companies affected by security breaches. Measures for adequate protection have become one of not only IT but also business priorities. Although employee education can help reduce the number of such cases, greater success can be achieved by using an additional authentication mechanism.
Elvis has been part of the STORM team since 2016 where he works on numerous projects of designing and implementing network solutions with an emphasis on security. In 2018, in addition to other Microsoft, Cisco, Fortinet, CompTIA certifications, he added CCIE # 58498 Enterprise Infrastructure certification in his resume. Before STORM Computers, he worked at Span, participating in numerous domestic and foreign projects to design and implement security solutions. CLI junkie since 2007. When Elvis’s not dealing with network security, he’s dedicated to family. He likes to spend his free time in nature, cycling, or hiking.
Cloud infrastructure pain points (from a sec perspective), visibility and compliance
by Matija Mandarić | .ops
Most common pain points of CISO, SecOps and security staff in general, when someone (DevOps? SysOps?) in the organisation is using cloud services or a hybrid infrastructure. The easy with which new services, functions, containers or VMs are spun up and used in some capacity or at least intersecting with infrastructure of the organisation is making even visibility very hard, not to mention securing those services. One way to automate these tasks and provide security teams with visibility and compliance will be mentioned in a short talk by Matija from TrendMicro.
From a security engineer to presales and consulting, enterprise security architecture and education. Matija has been in security for 10y know, in various roles and various organisations with various responsibilities, from a user through an integrator to a vendor. He likes to joke that it made him jack of all trades but master of none. But hey, as an SF author once wrote, specialisation is for insects?
How to achieve Privileged Access nirvana and avoid common mistakes?
By Robert Michalski | .tech
From physical safes with envelopes inside to automated, fully audited controls for various aspects of privileged access. Not only for human based access, but also for service and application accounts. This presentation is about how to start, what to focus on and what to avoid as highly processed food.
Robert Michalski is a security engineer with over 20 years of experience in the field on his neck. Developer from university education and security guy from the bottom of his heart. Declared opponent of marketing babble and babble at all. Proponent of independent, logical thinking. Always looking to take off shoes and play some beach volleyball.
Deciphering the Decentralized Crypto Ecosystem
by Shiran Kleiderman | .lead
Details TBA
Who should go deep with us?
- CEOs, COOs, CTOs and other Cs
- Corporate security managers
- Information security managers
- Chief information security officers
- IT admins
- Members of IT security teams
- Security operation center members
- Penetration testers
MBCOM Technologies is the exclusive representative for Broadcom Software (CA and Symantec software solutions) in five substantial territories – the Middle East, Turkey, Africa, Eastern Europe and Russia/CIS.
Broadcom Software is one of the world’s leading enterprise software companies, modernizing, optimizing, and protecting the world’s most complex hybrid environments. With its engineering-centered culture, Broadcom Software is a global software leader building a comprehensive portfolio of industry-leading enterprise software enabling innovation, stability, scalability, and security for the largest global companies in the world.
Veracomp is a regional representative of leading ICT companies, offering security, network, telecommunications and data center solutions. They have been present on the market since 2001, when they started distributing security solutions, and to this day they follow trends and continuously add leading companies to their portfolio. Through a long-standing presence in the Adriatic region, Veracomp offers pre-sales and technical support to its partners, as well as education and consulting services. The goal of Veracomp is to be an extended hand and support to partners in the entire business process and to provide services that ensure continuity and flexibility of work, security of data from threats and insight into the activities of system users.
Kodeks is for more than 30 years known as first Dell Distributor in Croatia. Over the years it has developed into one of the leading system integrators in the region and beyond. Through direct collaboration with global technology partners such as Dell, Cisco, Mitel and Bosch Kodeks delivers information technology, telecommunications, networking and security systems, integration services, maintenance and support. Kodeks’s customers are leading telecom operators, government institutions, hotels, finance institutions, commercial and global customers.
Nestec is a value-add distributor of cloud and on-premise solutions for managed service providers and IT professionals with focus on security, communication and documentation of IT environments. In our portfolio you will find well-known technologies and established vendors like Solarwinds, Altaro and Thycotic, as well as innovative vendors and technologies that set new trends, help retail partners and managed service providers to create new projects and improve their service offering. In addition to solutions we provide sales and technical trainings, business and marketing consulting, and support our partners in all phases of the sales and implementation process.
Businesses and governments rely on Thales to bring trust to the billions of digital interactions they have with people.
Thales identity management and data protection technologies help banks exchange funds, people cross borders, energy become smarter and much more.
More than 30,000 organizations already rely on Thales solutions to verify the identities of people and things, grant access to digital services, analyze vast quantities of information and encrypt data.
In early 2019, Thales acquired the international security company, Gemalto and have combined it with its existing digital assets to create a new leader in digital security. Every organization around the world is in the midst of a digital transformation and stands to benefit from their joint innovations.
As the world becomes more connected, Thales makes it more secure.
Trend Micro, a global cybersecurity leader, helps make the world safe for exchanging digital information. As a leader in cloud and enterprise cybersecurity, Trend Micro platform delivers central visibility for better, faster detection and response and a powerful range of advanced threat defense techniques optimized for endpoints, data centers, hybrid and cloud environments and networks. This powerful platform enables secure digital transformation, empowering you to focus on driving your business further. Fueled by decades of security expertise, global threat research, and continuous innovation, Trend Micro cybersecurity platform protects 500,000+ organizations and 250+ million individuals across clouds, networks, devices, and endpoints.
NETSCOUT provides IT and business teams a seamless and consistent level of visibility into the performance, availability and security risks that impede digital agility, regardless of the underlying platform, provider, or location.
Companies rely on NETSCOUT Smart Data to proactively monitor, triage, and protect service and application performance and security within our nGenius service assurance and analytic solutions, Arbor DDoS protection solutions and our Omnis Security solutions. 90% of Fortune 100 and Tier One service provider companies—rely on NETSCOUT to assure and protect the services which advance our connected world.
ThycoticCentrify is a leading cloud identity security vendor, enabling digital transformation at scale. ThycoticCentrify’s industry-leading privileged access management (PAM) solutions reduce risk, complexity, and cost while securing organizations’ data, devices, and code across cloud, on-premises, and hybrid environments. ThycoticCentrify is trusted by over 14,000 leading organizations around the globe including over half of the Fortune 100, and customers include the world’s largest financial institutions, intelligence agencies, and critical infrastructure companies.
© Thycotic Software, LLC and Centrify Corporation 2021. Centrify® and Thycotic® are registered trademarks of Centrify Corporation and Thycotic Software, LLC respectively.
Tijekom stoljeća djelovanja, KONČAR se od skromne radionice razvio u regionalnog lidera u području elektroindustrije i tračničkih vozila te jedan od nositelja razvoja u svom području djelovanja, ali i ukupnom domaćem gospodarstvu. Temeljna područja djelovanja su energetika, tračnička vozila i infrastruktura, digitalna rješenja, obnovljivi izvori, istraživanje, razvoj i inovacije te laboratorijska ispitivanja i certificiranja.
Ime KONČAR danas je prepoznatljivo diljem svijeta te je pojam visoke razine kvalitete i pouzdanosti. Oprema i postrojenja u 130 zemalja na svim kontinentima dokaz su upravo tih vrijednosti i trajni su spomenici dostignuća Grupe KONČAR. Više od 400.000 transformatora raznih vrsta, naponskih nivoa i snaga dio su distribucijskih i prijenosnih mreža diljem svijeta, a KONČAR je djelomično ili u potpunosti izgradio i revitalizirao 375 hidroelektrana diljem svijeta, proizveo i revitalizirao 700 generatora te proizveo i isporučio 200 niskopodnih tramvaja i vlakova.
U razdoblju koje je pred nama strateški prioriteti KONČARA fokusirani su na razvojno-inovacijski potencijal kompanije, na ključne proizvodne kapacitete i njihovu modernizaciju te daljnje jačanje sinergije cijele Grupe. KONČAR veliku priliku vidi u obnovljivim izvorima energije te dodatnom smanjenju štetnog utjecaja na okoliš, ali i iskoraku u digitalizaciji postojećih proizvoda i usluga te proizvodnih kapaciteta.
KONČAR i u godini velike stote obljetnice ide u korak sa suvremenim tehničkim i tehnološkim trendovima te zahtjevima izazovne elektroenergetske budućnosti.
Falkensteiner Punta Skala, hotel IADERA
Punta Skala bb, HR-23231 Petrčane
Email
info@deep-conference.com

Falkensteiner Hotel & Spa Iadera at Punta Skala Resort
the best suited mid-Dalmatian conference venue waits for the participants of very first DEEP

Venue
Looking for starting in very best possible manner, DEEP proudly presents an excellent venue for the first conference, to be held from 14th to 15th of April 2021. We are proud to welcome you to glorious five-star Falkensteiner Hotel & Spa Iadera
Hotel & Spa Iadera - part of famous Falkensteiner Punta Skala Resort, one of most respected tourist complexes in whole Adriatic area. Resort is conveniently situated just a short drive from vibrant city of Zadar but it also contains all the facilities any conference attendee might need during a stay. Even if this is first DEEP, we have huge experience in organizing similar events, and it assured us that single-point conference is the most convenient way for our guests and visitors to enjoy both the conference and any free time dedicated to themselves.

Apart from breath-taking location directly at the top of the Peninsula and exclusive 5-star service, at our chosen venue you can also enjoy Mediterranean cuisine with hotel restaurant, fish restaurant Bracera, Steak house Planika and Hideout beach bar directly at the sea.
Should you want to stay for the weekend, there are several great areas for visiting, from the ancient town of Zadar, famous - among other things - for the most beautiful sunset in the world, to the national parks of Velebit and Kornati or worldwide known sci-fi landscapes of island Pag.

We are looking forward to be your hosts at this magnificent hotel during the conference. Online registrations will start soon, offering you accommodation in single or double rooms at this hotel during the process, at special prices agreed with Falkensteiner Hotels & Residences, available only to the DEEP attendees. Should you have any additional questions please be free to ask us at info@deep-conference.com. We are sure that this venue will fully enhance your experience and make your stay there during DEEP more enjoyable.
A big Thank You! to all the DEEP participants
Dear DEEP participants,
We’d like to simply thank you for being there, enabling our first DEEP to happen. According to the initial responses, we might consider it a success and, hopefully, start of a new tradition. Even if it is over, it isn’t! In a few weeks we will open a new section on this website, one where you’ll bee able to hear or read the presentations, as well as look at the photos and videos from the conference. In the meantime, we are available for your questions and requests at all the usual means of contact.
Kind regards,
DEEP team