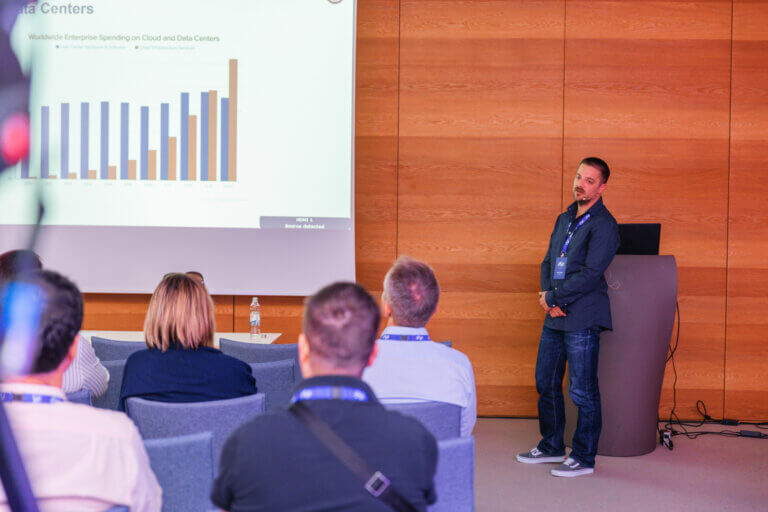
DEEP Conference
We recognized the need to address information security at all levels at the same time and the same place.
We value the importance of knowledge and experience sharing.
Therefore, we provide everyone with the opportunity to share their knowledge and build their new experiences. Dive in and go deep with us.
- Why go deep with us?
- Learn from experts and share your knowledge and ideas
- Share global and local trends
- Network
- Choose topics and tracks by yourself
- Initiate new projects and collaborations
- Who should go deep with us?
- Those who manage corporate and information security
- Folks from the IT and IT security
- Penetration testers
- SOC members from all levels

Drill down to the bit level
Technical and low level stuff is in the focus here. It might be a game for some, but various real-world attack simulations can be expected in here, as well as hacking, exploits and malware dissecting. New ideas on how to identify and exploit vulnerabilities are more than welcome.

Organize your protection!
A combination of technical and management stuff is in the focus here. How to orchestrate people, technology and processes to achieve maximum protection efficiency? Topics such as infrastructure protection, damage control, threat intelligence and incident response. Case studies can be found in this track.

Manage the risks, protect your business!
It’s all about management in here; governance, risk, compliance and business in general. Most of the people in here will try to get everyone on the same high-level page. It’s about understanding each other and dealing with future ideas and collaboration between business areas.
Ivica Kostelić - Pursuit of excellence
Robert Kopal - Cyber Risks Horizon






DEEP conference
































Pursuit of excellence
By Ivica Kostelić | Keynote presentation
The second keynote presentation at the beginning of DEEP, this one aimed for broader audience and not exclusively about the themes usually covered there – but definitely in touch with those. From his own experiences gathered through top sports career, expeditions and offshore sailing, Ivica will tell us about the search for personal growth, striving for excellence and share the lessons learned at the edge of the world and at the edge of one's capabilities.
Kostelić needs no introduction in Croatia, or in any country where the Alpine skiing is followed. Once an overall World Cup winner and multiple champion in both slalom and combination, he also won four silver Olympic medals over the course of his career. Since retirement he works with young skiers as an advisor for the Croatian national team. In recent years he developed a passion for offshore sailing, finishing his first trans-Atlantic regatta last year. Just a few weeks after DEEP conference he will take part in Route du Rhum, the most famous Atlantic crossing intended for single sailors.
Cyber Risks Horizon
By Robert Kopal | Keynote presentation
There are various risks: economic, ecological, social, geopolitical, technological etc. However, the true challenge is their interconnectedness. How to realize in time that “…a flap of butterfly’s wings in Brazil can set off a tornado in Texas…”?
Risk can be connected with the likelihood of the occurrence of an adverse event. However, it does not suffice to define the risk solely based on likelihood. The significance of the consequence must also be taken into consideration if such an event occurs. On the other hand, uncertainty is a circumstance where there is only awareness of the possibility that an adverse event will occur and no sufficient knowledge of its likelihood.
Can you imagine (hypothetically) the work of an intelligence analyst without any data on the likelihood of the outcome predicted? If there is no likelihood in it, then the likelihood can be defined within the scale ranging from “definitely won’t happen” to “definitely will happen”. These extremes correspond to zero (0%) likelihood and hundred (100%) likelihood.
The issue with calculating likelihood and predicting the consequences is the fact that human brain is not equipped with the “likelihood mode”. We are capable of intuitively and somewhat precisely estimating the height of most objects, their distance or dimension, or make other estimates based on visual perception. However, non-visual and non-tangible estimate of likelihood is often unreliable.
Although it is key to understand the likelihood concept and its use, due to the fact that likelihood intertwines with intelligence analysis, both explicitly and implicitly, the likelihood is a concept that we understand the least and that we find most difficult to use efficiently because likelihood laws are often counterintuitive.
We are too often in a phase of uncertainty, whereas we must reach a phase of risk, and after that a phase of risk management. A phase of uncertainty has to be followed by a phase of risk, and finally a phase of risk management has to be reached, for which human resources are the most important.
In this presentation the focus will be on Cyber Risks. What is on the Horizon? How to deal with it? Trend vs. microtrend? Why the utmost challenge in mastering Security Risks is to “defeat oneself”? What are the 4 components of Cyber Risk? What is Cyber Security Strategy Cycle? What can we do with Scenario Analysis? How to design EWS? How to build Cyber Resilience? What is the role of Intelligence Analysis in dealing with Cyber Risks? What is 3P model? What Prospect Theory has to do with Cyber Risks? What skills are vital for dealing with Security Challenges of the 21st century?
Robert Kopal, Ph.D., Assoc.Prof.
• Senior Research Associate; Tenured University College Professor; Chairman of the Board at EFFECTUS University College for Entrepreneurial Studies; Advisor of the Board at Tokić.
Professional and scientific experience:
• Special Advisor to the Prime Minister for National Security; Acting minister & State Secretary at Ministry of the Interior; Chief Intelligence Analyst at Ministry of the Interior and Senior Manager at the Security and Intelligence Agency; 3x Dean Effectus University College for Law and Finance; Vice Dean for R&D at Algebra University College and Head of the professional master study programs of Digital Marketing and Data Science; Vice Dean for Academic Affairs at Libertas
International University; Lecturer and visiting lecturer at numerous university colleges in Croatia and abroad and at CROMA EduCare Programme (Croatian Managers and Entrepreneurs Association); R&D Executive Director at Tokić; Advisor of the Board at IN2 Group for R&D/Science Advisor; Chief Science Officer at IN2data; Author of 13 books published in Croatia and abroad (Intelligence Analysis; Game Theory, Competitive/Business Intelligence Analysis Techniques, Analytical Management, Economic Analysis of International Terrorism, etc.); Author of a number of chapters in books and of about 70+ professional and scientific papers in Croatia and abroad; Head of, and lecturer at over a hundred business and analytical workshops in Croatia and abroad (trained intelligence & law enforcement officers from 11 countries); Head of PIU & Key Expert: “CARDS Twinning project: Criminal Intelligence System, Phase 1&2” te Project Liaison Officer na UNODC (United Nations Office on Drugs and Crime) projektu “Strengthening of Capacities for Collection and Analysis of Criminal Intelligence in South-eastern Europe”; 2 UNODC commendations; Designed several specialized IT systems; certified intelligence analysis techniques and intelligence analysis software trainer; Member of IALEIA (International Association of Law Enforcement Intelligence Analysts) and BDVA (Big Data Value Association); Editor-in-Chief of the International Journal of Digital Technology and Economy and member of the editorial board of the International Journal of Economics &; Management Sciences; Speaker at various national and international conferences; Participant and head of multiple national and international analytical projects; Member of the Agency for Science and Higher Education Commission for Social Sciences; Member of the National Council for the Development of Human Potential; Member of National Cyber Security Council; Member of the Croatian national team - European Big Data Hackathon 2017, which won the 1st prize, etc.; Last book Analytical management has won 2 awards.
Zero-Effort Zero-Trust for blocking Zero-Days in Kubernetes
By Darren Aitchison | .ops
Do security marketing buzzwords like “Zero Trust” trigger sales fatigue and anxiety? If so, then feel safe and secure with a demonstration of actual, real, automated Zero Trust security policies that are enforceable at network and process layers! Introducing Open Zero Trust, a new opensource project being forked from SUSE NeuVector which brings innovative security automation using network-centric, Deep Packet Inspection to auto-create Zero Trust security policies that do not rely on eBPF. OZT can define and enforce zero trust segmentation for network, processes and file access within any Kubernetes cluster without impacting performance, without impacting your service mesh, and is completely opensource! Sound impossible? Join Darren Aitchison, Sr Security Engineer from SUSE Neuvector as he demonstrates how OZT can block zero-day attacks at multiple layers within a kill-chain, automagically!
Darren has been working in the security space for over 20 years, since leaving the British Army. He specialised in network and application security working for a number of vendors and systems integrators. He has been with NeuVector for nearly 3 years as a Security Engineer.
Workshop: The Art of Cyber Threat Intelligence
By Bojan Alikavazović | .ops
Structured Analytical Techniques (SAT) and skills, as well as modern technologies for collecting and processing data, form a crucial combination for countering today's advanced attacks. Only up-to-date and relevant intelligence information can give you an advantage over an attacker. Despite all the technological advances, ultimately it is the analyst who creates the intelligence, not the device. Become an intelligence analyst for a day in this unique workshop and win a prize.
Bojan works as a security analyst at Diverto d.o.o. He is a member of the Security Operation Center (SOC) which monitors, processes and manages security incidents in various business environments. He has experience in threat research, reverse engineering of malicious code, penetration testing, security hardening, revision of network architecture with the aim of security improvement, and integration of various solutions for detection and blocking of cyber attacks.
eIDAS2 regulation as the foundation for next steps in EU digital transformation
By Marko Bobinac | .lead
Upcoming eIDAS update is a big Citizen Digitalization enabler with the major new (mobile) element – EU ID Wallet. We will be demystifying the upcoming regulation, look at the timelines and technical aspects.
Marko Bobinac is leading Thales’s Alliances in EMEA in the area of Payment and Trusted Services. Through the 10+ years in Thales Marko was working with all Encryption, Key Management and Authentication solutions from Thales CPL is portfolio. He has experience in Customer projects for securing Confidentiality, Integrity, Availability and Accountability with Network Encryption, Payment security solutions, modern PKI infrastructure, efficient Storage&File encryption, DB encryption, Data Anonymization and other encryption-based solutions. Marko is also one of the pillars of Thales’s eIDAS strategy for both Authentication and Hardware Security Modules product lines.
Region locks arriving
By Jurica Čular | .lead
Privacy shield is down, and the world has entered a phase of strict region/national data boundaries building. What does this mean for the companies working globally and what are the possible solutions to stay compliant?
Jurica Čular graduated at Faculty of electronics and computer science, Zagreb, Croatia as Master of Computer Science. Got an MBA in finance and marketing at Kelley School of Business, Indiana University. Holds several information security certificates like CISA, CISSP, ISO 27001 LA. Worked as an information security consultant for financial institutions and Big 4. Spent 9 years working as an expert advisor in Information Systems Security Bureau. Currently working as a Security Governance Expert in Infobip ltd.
Attack vector: peopleware
By Radoslav Dejanović | .lead
Disinformation is not just a societal problem: it can easily affect an organization. While it usually does not present a direct threat to an organization and does not involve high technical skills, disinformation can disrupt the processes in harmful ways. This is a light introduction to the ways disinformation can penetrate and disrupt a company - and what protective measures we may take.
Radoslav Dejanović started his career as an IT journalist before moving on to work in corporate and governmental environments, and ended up as an independent IT consultant. Throughout his career he never truly left journalism, having written numerous columns about both IT technology and social issues. He's the author of "Methods and tools for fact-checking of on-line media" (2020.), a free handbook aimed at helping people check for and recognize disinformation on the Internet; the e-book has been downloaded >8000 times.
Challenges in mobile digital forensics
By Saša Deković | .tech
Nowadays, there’s almost no crime committed where LE agencies can’t find a clue on a mobile phone. “Bad guys” need to communicate, and they leave traces on their favourite mobile phones. Sometimes it is easy to extract data from those digital gadgets, but sometimes examiners are stuck, because of a lack of experience, but sometimes examiners can’t do anything, because of unknown passwords or encryption.
The first problem is (especially in Croatia and in most of the EU countries), that in legislation, there’s no way to “force” a suspect person to give a password to unlock a mobile phone. It depends on the type and chipset in the mobile phone, we (mobile phone examiners), can’t do anything. Manufacturers of mobile phones are selling their new and expensive products with one of the most wanted features: “Your new phone is the most secured one and no one cannot break into your data, even us”.
Is it so?
We are aware that almost every day a new model of mobile phone is released with new security features, new chipsets, and new ways of encryption of your valuable data. Luckily, developers of the mobile phone extraction tools, don’t sleep much (unfortunately) and they find a way how to break a password or avoid system security settings. Those tools are usually very expensive and sometimes hardware requirements are very demanding, but if you have “A CASE” you need to use it, and luckily, you can extract all the data (almost) from the mobile phones.
Those challenges demand a lot of money, a lot of experience, and demands from examiners to be enthusiasts and try to do “everything” they know to extract data. Sometimes you fail, but sometimes you are “The lucky one” and you can extract all the data from mobile phones, to prove or disapprove that someone commit a crime.
Saša works in INsig2 as a consultant in the digital forensics department, where he is primarily responsible for forensic training and client education and for support during demanding and complicated investigations. Saša was involved in equipping and setting up several digital forensics laboratories. Due to his previous work experience in the Ministry of the Interior as a digital evidence forensic examiner, he has excellent knowledge of forensic tools and almost 15 years of experience consulting in digital forensics investigations as well as conducting them, especially in the field of mobile phone investigations. During his work in the Ministry, he worked in the field and planned police actions, and was involved in many criminal cases such as child exploitation, drug smuggling, economic fraud, and people smuggling.
Finding unique vulnerabilities with "depth" recon in modern web applications
By Josip Franjković | .tech
Modern web applications are increasingly complex, having a plethora of different technology stacks, APIs and functionalities, which makes properly testing the security of such applications harder and often tedious.
This presentation will show Josip’s approach when looking at complex web applications and techniques he uses to find new attack surface in the core parts of various real world applications, with a focus on discovering hard-to-find functionalities, legacy, region-locked, testing or partner APIs and so on.
The example bugs and bug chains in this presentation have been fixed, and were disclosed to affected companies through their bug bounty programs.
Josip Franjković is a freelance security researcher and a ""bug bounty hunter"". Throughout his career he has reported over 200 verified vulnerabilities to companies like Facebook, Google, Microsoft, PayPal, Yahoo and others, with a main focus on authentication and authorization vulnerabilities.
Josip is a top hacker on PayPal's bug bounty program, and tops Facebook's whitehat list in the '17-'19 period. He has also participated in live hacking events around the world for PayPal, Yahoo and Facebook, where he was asked to find vulnerabilities in yet to be released software and hardware, winning two ""Most Valuable Hacker"" awards and placing among the top three participants multiple times.
Securing Remote Workers - what happened to the security landscape in the last two years?!
by Vedran Franjić | .tech
Last two/three years were challenging for all organisations. Introduction to global quarantine made organisations look for new approaches to enabling their employees as remote workers as soon as possible. Having to adopt digitalisation at that pace, and yet again putting priority on connectivity over security, left a lot of holes in security which made a lot of successful attacks deployed in the last few years.
Through the session, we will explain how customers are solving this problem by moving security to the cloud, providing security anywhere for all remote workers, what best practices they are implementing and how Palo Alto Networks Prisma Access fits into this. Last part of the session will be reserved for the Prisma Access demonstration.
Vedran Franjić recently joined the Palo Alto Network organisation as Security Systems Engineer for Adriatic region. He has years of experience helping customers with designing, testing, troubleshooting and providing consultancy in the Security and SD WAN area.Prior to joining Palo Alto Vedran worked in Cisco as System Engineer, responsible for Security and SD-WAN. Holds a Master of Science in Electrical engineering and information technology, Computer Engineering FERIT, University of Osijek. He likes to spend his free time playing or watching any sport.
Preparing for cyber incidents and crises and introduction to the workshop
By Stjepan Groš and Goran Polonji | .ops
Managing significant incidents, and especially crises, is hard. But it’s not a question IF they’ll happen but WHEN. For that reason having a good incident management plan is mandatory, as well as being certain that it fits organization’s specifics and requirements and that everyone is ready to execute this plan. In this presentation we’ll talk about cyber security exercises as a mean to prepare organization for significant incidents, what makes them important tool for organizations as well as what makes good cyber security exercise. We’ll touch briefly on the most frequent types of cyber security exercises.
The main part of the presentation deals with Cyber Conflict Simulator that Utilis d.o.o. and Faculty of Electrical Engineering and Computing University of Zagreb co-developed as a part of research and development project. It is also introduction to workshop organized by Utilis d.o.o., Electrical Engineering and Computing University of Zagreb, and Croatian Military Academy "Dr. Franjo Tuđman".
Lastly, we’ll touch upon an initiative by International Society of Automation (ISA) which is coordinating and leading development of a framework to manage cyber security crises – Incident Command System for Industrial Control Systems (ICS4ICS). We’ll explain what this activity is about, what is the current status, and provide information on how to join this effort.
Stjepan Groš is assistant professor on Faculty of Electrical Engineering and Computing University of Zagreb. He’s head of a Laboratory for Information Security and Privacy where he’s principal investigator in several projects related to cyber security, with topics such as incident handling, security of industrial control system. His research interests are in applying advanced methods like AI/ML in solving cyber security issues. He’s a member of governing board of Croatian competitiveness cluster of defence industry in charge of cyber security.
Goran Polonji is an information security consultant and cybersecurity auditor in Utilis d.o.o. Last twenty years working with financial institutions and industry in improving information security posture and fulfilling regulatory compliance. He is a member of Cyber Conflict Simulator development team as a domain expert. Continuously trying to build understanding between business and technology experts about cybersecurity and to fill the gap between administrative and technical cybersecurity controls.
Security Graphics with Multilayered Elements in the Near-Infrared and Visible Spectrum for Urban Security
by Dr. Jana Žiljak Gršić I.tech | .ops
Jana Žiljak Gršić will present a new method of security printing of highly protected data. She is one of the authors of the Infrared design patent, which is a revolutionary technological solution for security data printing processes. The innovation refers to the application of the infrared effect in printing technology with the aim of preventing counterfeiting. The solution enables secure printing of data in two spectral regions; visual and infrared. It determines the generation of colour with completely different behaviour in areas affected by IR light. IR label detection is only possible with instruments that "see" at wavelengths above 700 nm and that can convert IR graphics into an object/image visible to the human eye. By using specific features that come from programming capabilities for digital and conventional printing, the algorithms are derived by including two or more colours that are the same colour (in daylight) but with completely different behaviour in IR light. The same image is separated by a dual algorithm, depending on the target visibility or invisibility in IR light. The modification of certain graphics protections is programmed, first for one and then another combination. The contribution is in the field of security for all data that are printed such as code, images on documents and securities, product traceability labels, as well as for archived files. She participated in numerous scientific researches in the field of graphic security, is the winner of the State Award for Science for 2010 for exceptional contribution to the development of science, and is an associate member of the Croatian Academy of Engineering. She is a permanent forensic expert for graphic technology, design, manuscripts, documents, securities, money, paintings, credit, and other cards. She is employed at TVZ and the University North. She teaches the study of Information Security and Digital Forensics at TVZ.
The allure and the darkness of Zero-Trust Networks
By Goran Kapić | .lead
Jana Žiljak Gršić will present an innovative solution, examples, and an algorithm for creating security graphics with the aim of increasing urban security. The solution is based on dual images that appear in the infrared and visible spectrum. In order to distinguish the information in the two light spectra, two inseparable images are created; a visible image, in which another image is integrated that is visible exclusively in the infrared spectrum. Examples for Urban security will be presented, including uniforms and documents of an individual solution with multi-layered protective elements. The implemented information is visible only to surveillance cameras and other infrared detectors. All graphics together make a security product with the characteristics of an individual solution with multi-layered protective elements. The solutions were created according to an algorithm based on the INFRAREDESIGN® method.
She participated in numerous scientific researches in the field of graphic security, is the winner of the State Award for Science for 2010 for exceptional contribution to the development of science, and is an associate member of the Croatian Academy of Engineering. She is a permanent forensic expert for graphic technology, design, manuscripts, documents, securities, money, paintings, credit, and other cards. She is employed at TVZ and the University North. She teaches the study of Information Security and Digital Forensics at TVZ.
Who Goes There?: Identity as We Know It is About to Change --XPM--
By Tomasz Joniak | .tech
Privileged Accounts are known to be the number one target for hackers as they represent the keys to the kingdom. This is why managing and securing these accounts should be at the core of every enterprise security roadmap. We will discuss how security projects don't always have to come at the cost of high overheads and additional management controls, and how following the best practices should be seamless and result in drastically reducing the attack surface for organizations.
High level agenda:
- Understanding of the business risks
- The cyber security landscape
- The Challenges of managing privileges
- The Modern PAM approach and solution
- The Best Practices and Maturity Model
- Your trusted partner: Delinea
Tomasz is a Sales Engineer for Delinea, focusing on securing privileged accounts across the landscape of technology; born in Poland, grew up in Chicago & now, after 30+years, he relocated back to Poland for his next adventure. Tomasz has extensive 18+ years of working for major IT partners such as WWT, Insight Global, and LaSalle Solutions (now Trace3) as Security Engineer; relocating to Poland, Tomasz joined Cisco Systems as Sr Security Consulting Engineer and TME, where he focused on ISE and Firepower. With his experience, Tomasz joined Delinea to identify and evaluate complex business and technology risks, internal controls which mitigate risks, and related opportunities for internal control improvement utilizing the Mature PAM model to meet today's IT complexities, as proven by the increase in cyberattacks. When not trying to be a Network Security Magician, he visits Historical European ruins with family.
OneID - Secure online authentication, identity verification, and electronic signatures
By Viktor Krstevski | .lead
EU EIDAS compliant electronic identification and electronic signature solution presentation following best practices in online identity management and interoperability with TRUSTED online (mobile, web) applications such as online banking services, and government e-services portals. Real-time, secure, traceable, user-controlled exchange of verified credentials between issuers, users and verifiers.
Viktor is technology manager with 10+ years of background in product and service development and delivery in telecommunications and SaaS companies. Extensive experience in digital transformation projects, online services development and operations with a strong focus on secure online payments&wallets, electronic identity and electronic signatures solutions. Currently responsible for electronic signatures and electronic identity product and services portfolio development at Nextsense.
Third Party Cyber Risk Management for Austria's critical infrastructure: How Austria's CISOs teamed up with industry and government.
By Alexander Mitter | .lead
Supply Chain Cyber Risks made news way too often recently. It is the new frontier once cybersecurity has been established within your own organization! The basic question is: How can we make sure that our digitally integrated suppliers are not our biggest security vulnerability? NIS, GDPR and DORA are further increasing the pressure on CISOs to look into their supply chain on top of their everyday tasks.
In Austria, we used EU-NIS requirements as a starting point for an extremely productive cooperation: We brought together CISOs, NIS authority and the cybersecurity industry to define a common standard for TPCRM. This standard serves as a guideline for suppliers and is used for cyber-risk ratings. It is enforced through audits and recognized by authorities. The best part about it: It is as simple as possible and freely available.
Too good to be true?
Alexander Mitter is co-founder and CEO of KSV1870 Nimbusec GmbH. Over the last 10 years the company established itself from start-up out of Linz to a major player in the Austrian Cyber Security landscape with a subsidiary in Munich, Germany. In 2019 Alexander initiated the national cooperation leading to the CyberRisk Rating and its ecosystem.
Simulating Advanced Persistent Threats (APT's) in virtual environment
By Tomislav Murat | .ops
Is your organization ready to face sophisticated adversaries? Find out the ways of automating process of simulating/emulating advanced threats in virtual environment. How to effectively use available methods of threat modeling of advanced threats with the aim of finding vulnerabilities and weaknesses of information systems and use the gained insight to better your existing security controls and detection procedures. How to use threat emulation/simulation tools in support of cyber exercise scenarios.
Tomislav Murat works in Government CERT department of Information Systems Security Bureau (ISSB) on prevention and response to computer security incidents with a purpose of achieving higher level of information systems security using acquired competences and experience. Has 11 years of experience working in the field of cyber security (digital forensics, system analysis, vulnerability and penetration testing). Graduated at Zagreb University of Applied Sciences - specialist study program „Information security and digital forensics”. Holds several information security and IT certificates.
Cyber Security in the Multi-Cloud Chaos era
By Elad Paz | .tech
Over the years Cyber Security moved to the center of the stage for organizations seeking to be relevant in the 21stcentury digital world. Cyber Security has grown to be more complex, detailed, multi-disciplinary, challenging while intruding unified concepts and methodologies to make sense to it all.
Join me to find out if your Cyber Security strategy fits the Multi-Cloud Chaos. What are the challenges, the risks and the solutions?
Elad Paz is part of VMware’s Cyber Security Center of Excellence (CoE) team. In his professional journey Elad started from the worlds of System Administration & technical support moving from there to Cyber Security and focusing on emerging technologies, Security architecture and leading Cyber technologies teams. In his current role Elad shares his 20+ years of Cyber security experience with Customers and Partners to support their Digital Transformation journey.
Internet Routing Security
By Ivan Pepelnjak | .tech
While we had the necessary means and technologies to significantly enhance the routing and packet forwarding security in the Internet for years if not decades, we’re still facing BGP hijacks and amplification DDoS attacks on daily basis.
This talk will describe some of the reasons for this dismal state of affairs, the steps one can take to increase the Internet routing security, and the MANRS framework that can guide you on that journey.
Ivan Pepelnjak, CCIE#1354 Emeritus, is a 30-year veteran of the networking industry, with 25+ years of experience in designing, installing, troubleshooting, and operating large service provider and enterprise WAN and LAN networks. He is currently an independent network architect at ipSpace.net AG, focusing on network automation, software-defined networking, large-scale data center and network virtualization technologies, and advanced IP-based networks.
Ivan is the author of a series of highly successful webinars and online courses. His books published by Cisco Press include MPLS and VPN Architectures and EIGRP Network Design.
Cyber security paradox and how to avoid it
by Robert Petrunić | .ops
The times we are living in are challenging and they require different approach to secure our systems. Ironically, never in history of humankind we had as secure systems as today, and yet, it is easier to compromise these systems then it ever was. Find out the author’s view into the main reasons why. The question we will try to answer is what we can do to change this trend by presenting the "paranoid" model the author is using on his laptop computer to protect and isolate the customer’s data on the security consultancy and penetration testing engagements. Even though the model is designed for a specific case, bits and pieces are more than usable for day-to-day work of IT professionals and the like. Enjoy the demo showing you the example on how easy it is to implement such a model, which will (together with the lecture) probably force you to rethink the way you are using your computer today and (hopefully) make you change it.
Robert works as a senior information security consultant in Eduron IS and he’s a lecturer in most successful Croatian private college Algebra. He’s Microsoft certified trainer since 2002, EC-Council certified trainer since 2008 and ISC2 certified trainer since 2014. Since 2004. Robert is working on programs related to ethical hacking and IT security awareness for systems administrators, developers and IT security consultant.
Information Security and the new Decision on Adequate Information System Management
By Slaven Smojver | .lead
Regulation is probably the main driver of changes in the financial sector. The new "Decision on Adequate Information Systems Management" that will apply from the 1st of April 2023 will significantly change the regulatory framework related to information security in all the banks in Croatia. This session will present the new obligations related to information security, including specific requirements on penetration testing, vulnerability assessment, end point security, data loss protection, file integrity controls, intrusion detection systems and many others.
As this is a locally-oriented content, concerning Croatian financial sector regulation, the lecture will be held in Croatian.
Slaven Smojver is director of the Information Systems Supervision Department in the Croatian National Bank (HNB). The department's primary responsibility is supervision and assesment of IT risk in credit institutions, e-money institutions, payment institutions, payment systems and FinTech companies. Slaven obtained his Ph.D., M.Sc. and M.Eng.EE degrees from the University of Zagreb, Croatia. He authored several scientific papers and has presented extensively on various topics related to financial services supervision, control and management of information system and information security in financial institutions. He is CRISC, CISA and CISM in good standing.
QUIC protocol - a new protocol that makes Firewall blind (in Croatian)
By Karlo Šagut | .tech
Things have changed recently on the Internet, HTTP/3 has been standardized and everything is encrypted with QUIC. Everything you need to know about a new encrypted-by-default Internet transport protocol - what is QUIC protocol, what is it used for and what are the network management and security implications.
Welcome to the new world of network troubleshooting and security.
Karlo Šagut is a network security engineer in Storm Computers d.o.o. Started his career six years ago as a network field engineer, and after two years promoted on a network security engineer position. Karlo has been working on many different projects since than with numerous products and vendors. When Karlo takes a break from work or studying, he spends time with his family or plays football.
I'll be watching you
by Dalibor Dosegović | .lead
Do walls have ears (and eyes)? What could be out there watching us or listening, in the office or in some other room? Answers to these questions, and many more you’ve had no one to ask…
After having spent almost 19 years on government salary, Dalibor decided to let loose and test his luck in the same line of work in the private sector.
Apple Security Research Device
By Antonio Zekić | .tech
Antonio's lecture 'Apple Security Research Device' will provide a general introduction to specially fused iPhone that allows security researchers to perform research on the latest version of iOS without having to defeat or disable the platform security features of iPhone.
Antonio Zekić is a senior information security consultant in Diverto d.o.o. He is experienced in penetration testing and reverse engineering. In spare time he enjoys fuzzing, exploit writing with an emphasis on iOS/macOS vulnerability research. He is a regular speaker at the security events in the region.
Diverto SOC and incident "war stories"
By Ivan Špoljarić | .ops
Security is never easy, it is better to say that perfect security is an impossible task. Every organization can expect a breach or malware infection. Due to the nature of more aggressive and more sophisticated environments we find ourselves in, mature organizations are required to up the ante of preparedness for challenges. Security Operating Center is at the core of preparedness for future.
This talk will try to paint the picture of a modern approach to Security Operating Center, with brief overview of components, personnel, procedures, and challenges. Components will be presented with a real-world scenarios where certain organizations succeeded or failed.
Purple colored security
By Vlatko Košturjak | .tech
Red team tests the security defenses of an organization, while Blue team is working on the security controls and defense itself. Red and Blue teams are often completely two separate teams often divided in pillars. While they can be distinct entities on the organizational chart, their collaboration is crucial for faster security improvement. Such collaboration is often called Purple Teaming and it became common practice to involve both red and blue teams in ultimate goal of securing the organization. It is not the path without bumps and dead ends, so it is about time to learn about experiences and industry best practices.
Vlatko Košturjak is Chief Technology Officer (CTO) at Diverto, where he helps clients to reach desired security level(s) with more than 20 years of experience in both breaking and building security controls from embedded systems to enterprise systems and networks. Beside security, his passion is open and free software, so he authored own tools for security purposes and contributed code to various popular free security software like Nmap, OpenVAS, Metasploit, etc. If you place your trust only on certificates, during his long career in information security, Vlatko gained CISSP, CISA, CISM, CRISC, CDPSE, MBCI, C|EH, OSCP, etc.
Blueprint for Zero Trust
By Davor Perat | .ops
Traditional perimeter defenses have been disappearing as organizations shift applications and workloads from on-premise data centers to cloud infrastructure. These technologies were never meant to scale to handle the large numbers of remote workers. A Zero Trust architecture is designed to address these challenges; however, organizations are struggling to integrate the different pillars of Zero Trust into a consolidated platform. In this presentation we will explain how to achieve zero trust with Symantec Integrated Cyber Defense
Davor Perat is handling pre-sales activities for Symantec Enterprise Division in a Senior Technology Consultant position since 2012. Currently employed at MBCOM Technologies, Broadcom Software Representative in the region. Member of a regional sales team, covering Adriatic countries.
Rise of non-detection-reliant technologies
By Mikolaj Pigon | .ops
Join us at this presentation, where one of the attendees will get a free pass for RISK Summit 2023!
Most of us used to love to play hide’n’seek when we were children. Didn’t we? The thrill of choosing the right spot, excitement in anticipation “will I be found?” and then run towards the spot to either win or lose. Hackers still play it. And digitalization makes their playground bigger and bigger… Zer0-days, steganography, obfuscation, polymorphic malware, environmental awareness – those are just a few “hiding tricks” that can be used to fool our security technologies. Their malware can remain hidden to our traditional detection based approaches like AV and Sandboxes and this is why need a new way to overcome the malware they have hidden.
You will learn that there are technologies with 100% accuracy. That these technologies have been widely used – just not in the industries operating in the limelight. And that “Zero-Trust” can be applied to erase ALL threats.
Mikolaj Pigon, Forcepoint Account Manager responsible for managing Customer relationships with organisations across South-East Europe. Deeply involved in regional channel ecosystem sharing knowledge, facilitating technical engagements and generally doing whatever it takes in sane borders to assure Customer satisfaction. Main area of interest is data & cloud security, IT security as a business ecosystem and philosophy. Passionate public speaker and aspiring copywriter. Educational background starts with management, currently ends in cybersecurity management and to be continued.
Cybersecurity in 3rd party mgmt
By Alberto Gusella| .lead
Third Party Risk Management is a strategic pillar for all Companies. As Digitalization initiatives accelerate, cyber risk aspects are becoming more important than ever. Join this speech to get more insights to the main trends and challenges for Cyber Security in TPRM.
Alberto Gusella is CSO in Zagrebačka banka, with 20+ years on experience in Cyber and Information Security, in PwC and Symantec before joining UniCredit Group.
Behavioral Economics of Information Security
By Darija Korkut | .lead
“The key to understanding cybersecurity is to think ahead and to take the steps that your future self would regret not taking.” - Kazi Kabir
Behavioral economics deals with decision making of “real” people as opposed to mythical rational creatures of neoclassical economics. It is grounded in empirical observations of human behavior, which have demonstrated that people do not always make “rational” or “optimal” decisions, even if they have the information and the tools available to do so. We are subject to emotion and impulsivity and influenced by the environment and circumstances. Our decisions are influenced by our perception and guided by our intuition. We are neither rational, nor logical, nor objective.
What does it have to do with information security? How does behavioral economics align with it?
Approximately 95% of cyber-attacks and events involve preventable human error and behavior weakness. Cybercriminals, for example, use phishing and social engineering to defeat data and system security by exploiting those errors in human judgement and weaknesses in behavior.
Another aspect in which behavioral economics can help is influencing opinion at the top about the potential gains and cost savings of investing in an information security program. We can break decision making in information security down to 1) event-based decision-making, which is in direct response to an event or incident - an alert is triggered that requires a prescribed action. This approach is faster, tactical, and necessary for day-to-day choices; and 2) risk-based decision-making, which we apply to determine where we should make strategic investments to minimize the volume of event-based decisions.
Humans have developed the ability to make these decisions quickly through heuristics and (cognitive) biases. We are cognitive misers; we do not waste our time on processing every piece of information with the same effort.
Also, our instincts inform our perception of security. Unfortunately, the statistics shows that the way we perceive security does not always square with reality and our response to risks is often far from adequate. With a basic understanding of how our brain processes information and by understanding how we arrive at a decision, we can considerably improve the security decision-making process.
For an industry which “exists” because of vulnerabilities of human behavior, there is no better cure for future challenges than behavioral economics.
Darija Korkut, mag. angl., Senior Lecturer, doctoral student of Information Society at the Faculty of Information Studies in Novo Mesto, Slovenia. She was working at the Ministry of Foreign and European Affairs, as an information and analysis officer, and as a diplomat at the Croatian Embassy in Dublin. In her 10-year experience at the Security Intelligence Agency she was working on analytical education and training, and the development of innovative technological solutions. In January 2019, she joined University College Effectus, where she teaches Analytical Management, Critical Thinking, Behavioral Economics, Psychology of Decision Making, and Decision Making under Risk and Uncertainty. Darija has co-authored eight books, and a number of professional and scientific papers on analytical methods and techniques and their application, primarily in business surroundings, game theory, social network analysis, creativity, and behavioral economics. She is the editor of Robert Kopal's book Economic Analysis of International Terrorism, also authoring the chapter titled "Application of Social Network Analysis (SNA) in Combating International Terrorism". She has participated in numerous domestic and international courses, seminars, and conferences in the field of international relations and diplomacy, and various analytical courses and workshops (NATO, US EUCOM, FBI among other), and as a lecturer at many of those. She owns international certificates in structured analytical techniques and critical thinking. Areas of interest: creativity and innovation, critical thinking, problem solving, behavioral economics, social network analysis, game theory, intelligence analysis, analytical management.
The importance of Incident response reports within the recovery of identity environments after cybersecurity attacks
By Tomislav Poljak| .ops
Incident Response reports, after cyber security attacks, are rarely made public, and therefore the publication of several recent reports has generated a lot of public interest. We will use this type of information in the session to explain the importance and content of a good Incident Response report for the subsequent recovery of the Identity systems. Through the session, we will show a demo with the real-time detection of cyber-attacks and minimal procedures for live containment of Active Directory.
This includes investigation, recovery planning, critical hardening, and tactical monitoring. During the session, you will also see that the technical expert skills and knowledge to do this kind of work are not enough, and it’s necessary to have the exceptional social skills to solve many stressful situations.
Tomislav works at Microsoft Croatia (for the past eleven years) and as a cyber security consultant has experience in the recovery of enterprise systems after cyber attacks. At a time without reactive engagements, he helps customers to establish SOC environments and carries out various engagements like monitoring, protection, and prevention to increase their security.
He often speaks at conferences in Croatia and the near region. He’s Microsoft certified trainer (MCT) since 2008 and hold other industry certificates. Whenever possible he spends time in nature, in any leisure or work activities.
TrendMicro V1; one and a half year after. Is it really more than just an XDR?
By Emilije Strahinja| .ops
This session is based purely on a true story :) Being a financial institution with friendly products means also being attractive to the bad guys too. How can you protect your landscape if you have a couple of hundred servers published over the internet, a few thousands of users and many many services relying on IT offered to the public? Can you match the balance between transparency and security features? Will classic antivirus do the job in the year of 2022, or do you need something to go deeper? In this session, we'll speak about layers of protection and focus on how TrendMicro VisionOne perfectly fits into this story. Also, we'll show some cool features it has, and how to effectively use it. We will also show some other cool features TrendMicro has, such as sandboxing.
Emilije Strahinja works in Croatia osiguranje as a security engineer, in ICT department. Emilije is a part of a great team who monitors, prevents, detects and responds to security threats. He has more than 14 years of experience in IT, working as system engineer with various technologies. As time changed and new challenges arise, over the last few years he shifted toward security technologies.
Workshop: Roles and Communication during Serious Cyber Incident in an Operator of Essential Services
By Utilis, FER and HVU | .tech
Do you know what it's like to be a victim of a sophisticated cyberattack? Do you know who should participate in solving the attack and who has what task? Do you know who you should report to and from whom you should receive information? Do you know what it looks like when you need to ensure business continuity and you have almost no information about what is happening? Do you know what it's like when everything is working right now, but at any moment critical services can stop?
During this workshop, all workshop participants will be divided into the roles of incident handlers, owners of business functions or members and president of the management board of a critical service operator. Your company will find itself under a sophisticated attack by an APT. The task you and other participants will have will be to ensure business continuity, while in the same time find the attacker in the network, and remove him so that your company can continue normal operations.
The goal of this workshop is to learn who should do what during an incident and with whom each participant should communicate. At the same time, this is a simulated situation and the attackers will not be so merciless, but they will still give you some headaches – exactly as much as it takes to feel what it's like to be under a cyber attack and what happens during it.
The workshop will last up to two hours, depending on the interest of the participants and the speed with which the incident is handled. In order to make the workshop as effective as possible, all registered participants will be assigned roles based on their actual business responsibilities in the organizations they come from.
The workshop is organized, conducted and technically supported by: Nikola Biliš (Utilis d.o.o.), Zdenko Čorić (Utilis d.o.o.), Dalibor Gernhardt (HVU), Stjepan Groš (FER), Ivan Kovačević (FER), Ida Krešo (FER), Goran Polonji (Utilis d.o.o.), Bruno Štengl (FER), Vito Žuvanić (Utilis d.o.o.).
This workshop is the result of two EU-funded projects. One that is completed and its result is the Cyber Conflict Simulator, a tool used for the simulation. Another ongoing project is the Center of Competences for the Security of Control Systems, in the context of which this exercise was developed.
If you are a registered DEEP attendee, please be free to reserve your workshop seat at https://forms.gle/LZwk6FA4KCjLv7kC8.
All about locks - a neglected side of security (powered by Perger)
Known in the world under the pseudonym" Lockpicking ", this is a demonstration of the physical protection of spaces and buildings where the weaknesses of various locks and similar locking equipment are easily visible and displayed. The DEEP participants will have the opportunity to try opening the locks of various security standards with the support of Mateo Benceković from the Lock opening craft "Perger" and will be able to clearly see the weaknesses of the locks and their protection. The aim of this part of the conference is to raise awareness of the need to protecting the physical space from the perspective of information security and beyond the scope of procedures, processes and protections of IT systems alone.
Who should go deep with us?
- CEOs, COOs, CTOs and other Cs
- Corporate security managers
- Information security managers
- Chief information security officers
- IT admins
- Members of IT security teams
- Security operation center members
- Penetration testers
MBCOM Technologies is the exclusive representative for Broadcom Software (CA and Symantec software solutions) in five substantial territories – the Middle East, Turkey, Africa, Eastern Europe and Russia/CIS.
Broadcom Software is one of the world’s leading enterprise software companies, modernizing, optimizing, and protecting the world’s most complex hybrid environments. With its engineering-centered culture, Broadcom Software is a global software leader building a comprehensive portfolio of industry-leading enterprise software enabling innovation, stability, scalability, and security for the largest global companies in the world.
MBCOM Technologies, Broadcom Representative is the sole representative for Broadcom Software (CA and Symantec Cyber Security solutions) in five substantial territories – the Middle East, Turkey, Africa, Eastern Europe and Russia/CIS.
Broadcom Software is one of the world’s leading enterprise software companies, modernizing, optimizing, and protecting the world’s most complex hybrid environments. With its engineering-centered culture, Broadcom Software is a global software leader building a comprehensive portfolio of industry-leading enterprise software enabling innovation, stability, scalability, and security for the largest global companies in the world.
Veracomp is a regional representative of leading ICT companies, offering security, network, telecommunications and data center solutions. They have been present on the market since 2001, when they started distributing security solutions, and to this day they follow trends and continuously add leading companies to their portfolio. Through a long-standing presence in the Adriatic region, Veracomp offers pre-sales and technical support to its partners, as well as education and consulting services. The goal of Veracomp is to be an extended hand and support to partners in the entire business process and to provide services that ensure continuity and flexibility of work, security of data from threats and insight into the activities of system users.
Kodeks is for more than 30 years known as first Dell Distributor in Croatia. Over the years it has developed into one of the leading system integrators in the region and beyond. Through direct collaboration with global technology partners such as Dell, Cisco, Mitel and Bosch Kodeks delivers information technology, telecommunications, networking and security systems, integration services, maintenance and support. Kodeks’s customers are leading telecom operators, government institutions, hotels, finance institutions, commercial and global customers.
Nestec is a value-add distributor of cloud and on-premise solutions for managed service providers and IT professionals with focus on security, communication and documentation of IT environments. In our portfolio you will find well-known technologies and established vendors like Solarwinds, Altaro and Thycotic, as well as innovative vendors and technologies that set new trends, help retail partners and managed service providers to create new projects and improve their service offering. In addition to solutions we provide sales and technical trainings, business and marketing consulting, and support our partners in all phases of the sales and implementation process.
Businesses and governments rely on Thales to bring trust to the billions of digital interactions they have with people.
Thales identity management and data protection technologies help banks exchange funds, people cross borders, energy become smarter and much more.
More than 30,000 organizations already rely on Thales solutions to verify the identities of people and things, grant access to digital services, analyze vast quantities of information and encrypt data.
In early 2019, Thales acquired the international security company, Gemalto and have combined it with its existing digital assets to create a new leader in digital security. Every organization around the world is in the midst of a digital transformation and stands to benefit from their joint innovations.
As the world becomes more connected, Thales makes it more secure.

STORM Computers je vodeća hrvatska tvrtka u području sistem integracije, razvoja, implementacije te održavanja kompleksnih i cjelovitih poslovnih informacijsko-komunikacijskih sustava.
Već preko 30 godina jedinstvenom kombinacijom tehnološkog znanja i vrhunske usluge postavljaju nove standarde izvrsnosti u primjeni najnovijih ICT rješenja.
STORM Computers kroz dugogodišnja partnerstva s vodećim svjetskim tehnološkim vendorima i praćenjem najnovijih trendova stalno dokazuje da je jedan od lidera na tržištu što pokazuje i prestižna nagrada - European Business Awards u kategoriji inovativnosti.
Njihova ponuda sastoji od pet glavnih područja – mrežna infrastruktura, sistemska infrastruktura, sigurnosna te rješenja za digitalizaciju i transformaciju poslovanja.

INGRAM MICRO
Ingram Micro helps businesses fully realize the promise of technology™—helping them maximize the value of the technology that they make, sell or use. With its vast global infrastructure and focus on cloud, advanced and specialty technology solutions, in addition to mobility and commercial/consumer technologies, Ingram Micro enables business partners to operate more efficiently and successfully in the markets they serve. Additionally, Ingram Micro provide IT Asset Disposal (“ITAD”) and Reverse Logistics and Repairs services to advance environmental sustainability through responsibly collecting and beneficially repurposing e-waste through remanufacturing, recycling, refurbishing and reselling technology devices.
DELINEA
delinea
Delinea is a leading provider of privileged access management (PAM) solutions that make security seamless for the modern, hybrid enterprise. Our solutions empower organizations to secure critical data, devices, code, and cloud infrastructure to help reduce risk, ensure compliance, and simplify security. Delinea removes complexity and defines the boundaries of access for thousands of customers worldwide. Our customers range from small businesses to the world's largest financial institutions, intelligence agencies, and critical infrastructure companies.
50 Word: Delinea believes every user should be treated like a privileged user and wants seamless, secure access, even as administrators want privileged access controls without excess complexity. Delinea’s solutions empower seamless security for the modern, hybrid enterprise with privileged access management (PAM) solutions that define the boundaries of access. With Delinea, privileged access is more accessible.

Nimbusec is an Austrian cloud service located in Linz, which checks web spaces and domains for malware, defacements and blacklisting from external sources.
In addition, Nimbusec works with a highly specialized server agent that can detect web shells and malware on your system. If potential manipulations are found, the message center informs within three minutes via e-mail or SMS.
Nimbusec was born from a real challenge: What is the best way to keep a large number of decentrally managed websites secure while maintaining data protection?
We asked this question when we were running servers for hundreds of websites of an Austrian university. Students and affiliated offices operated a large number of content management systems, which were often barely updated. This led to many successful cyber attacks, but due to university policy, administrators were not allowed to read or write data in user directories.
We therefore developed a solution that used public information only in conjunction with a machine-generated, abstract code-behavioral description to detect malware, defacements and blacklisting: Nimbusec was born.
Trend Micro, a global cybersecurity leader, helps make the world safe for exchanging digital information. As a leader in cloud and enterprise cybersecurity, Trend Micro platform delivers central visibility for better, faster detection and response and a powerful range of advanced threat defense techniques optimized for endpoints, data centers, hybrid and cloud environments and networks. This powerful platform enables secure digital transformation, empowering you to focus on driving your business further. Fueled by decades of security expertise, global threat research, and continuous innovation, Trend Micro cybersecurity platform protects 500,000+ organizations and 250+ million individuals across clouds, networks, devices, and endpoints.
NETSCOUT provides IT and business teams a seamless and consistent level of visibility into the performance, availability and security risks that impede digital agility, regardless of the underlying platform, provider, or location.
Companies rely on NETSCOUT Smart Data to proactively monitor, triage, and protect service and application performance and security within our nGenius service assurance and analytic solutions, Arbor DDoS protection solutions and our Omnis Security solutions. 90% of Fortune 100 and Tier One service provider companies—rely on NETSCOUT to assure and protect the services which advance our connected world.
ThycoticCentrify is a leading cloud identity security vendor, enabling digital transformation at scale. ThycoticCentrify’s industry-leading privileged access management (PAM) solutions reduce risk, complexity, and cost while securing organizations’ data, devices, and code across cloud, on-premises, and hybrid environments. ThycoticCentrify is trusted by over 14,000 leading organizations around the globe including over half of the Fortune 100, and customers include the world’s largest financial institutions, intelligence agencies, and critical infrastructure companies.
© Thycotic Software, LLC and Centrify Corporation 2021. Centrify® and Thycotic® are registered trademarks of Centrify Corporation and Thycotic Software, LLC respectively.
Tijekom stoljeća djelovanja, KONČAR se od skromne radionice razvio u regionalnog lidera u području elektroindustrije i tračničkih vozila te jedan od nositelja razvoja u svom području djelovanja, ali i ukupnom domaćem gospodarstvu. Temeljna područja djelovanja su energetika, tračnička vozila i infrastruktura, digitalna rješenja, obnovljivi izvori, istraživanje, razvoj i inovacije te laboratorijska ispitivanja i certificiranja.
Ime KONČAR danas je prepoznatljivo diljem svijeta te je pojam visoke razine kvalitete i pouzdanosti. Oprema i postrojenja u 130 zemalja na svim kontinentima dokaz su upravo tih vrijednosti i trajni su spomenici dostignuća Grupe KONČAR. Više od 400.000 transformatora raznih vrsta, naponskih nivoa i snaga dio su distribucijskih i prijenosnih mreža diljem svijeta, a KONČAR je djelomično ili u potpunosti izgradio i revitalizirao 375 hidroelektrana diljem svijeta, proizveo i revitalizirao 700 generatora te proizveo i isporučio 200 niskopodnih tramvaja i vlakova.
U razdoblju koje je pred nama strateški prioriteti KONČARA fokusirani su na razvojno-inovacijski potencijal kompanije, na ključne proizvodne kapacitete i njihovu modernizaciju te daljnje jačanje sinergije cijele Grupe. KONČAR veliku priliku vidi u obnovljivim izvorima energije te dodatnom smanjenju štetnog utjecaja na okoliš, ali i iskoraku u digitalizaciji postojećih proizvoda i usluga te proizvodnih kapaciteta.
KONČAR i u godini velike stote obljetnice ide u korak sa suvremenim tehničkim i tehnološkim trendovima te zahtjevima izazovne elektroenergetske budućnosti.
Falkensteiner Punta Skala, hotel IADERA
Punta Skala bb, HR-23231 Petrčane
Email
info@deep-conference.com

Falkensteiner Hotel & Spa Iadera at Punta Skala Resort
the best suited mid-Dalmatian conference venue waits for the participants of very first DEEP

Venue
Looking for starting in very best possible manner, DEEP proudly presents an excellent venue for the first conference, to be held from 14th to 15th of April 2021. We are proud to welcome you to glorious five-star Falkensteiner Hotel & Spa Iadera
Hotel & Spa Iadera - part of famous Falkensteiner Punta Skala Resort, one of most respected tourist complexes in whole Adriatic area. Resort is conveniently situated just a short drive from vibrant city of Zadar but it also contains all the facilities any conference attendee might need during a stay. Even if this is first DEEP, we have huge experience in organizing similar events, and it assured us that single-point conference is the most convenient way for our guests and visitors to enjoy both the conference and any free time dedicated to themselves.

Apart from breath-taking location directly at the top of the Peninsula and exclusive 5-star service, at our chosen venue you can also enjoy Mediterranean cuisine with hotel restaurant, fish restaurant Bracera, Steak house Planika and Hideout beach bar directly at the sea.
Should you want to stay for the weekend, there are several great areas for visiting, from the ancient town of Zadar, famous - among other things - for the most beautiful sunset in the world, to the national parks of Velebit and Kornati or worldwide known sci-fi landscapes of island Pag.

We are looking forward to be your hosts at this magnificent hotel during the conference. Online registrations will start soon, offering you accommodation in single or double rooms at this hotel during the process, at special prices agreed with Falkensteiner Hotels & Residences, available only to the DEEP attendees. Should you have any additional questions please be free to ask us at info@deep-conference.com. We are sure that this venue will fully enhance your experience and make your stay there during DEEP more enjoyable.
Businesses and governments rely on Thales to bring trust to the billions of digital interactions they have with people.
Thales identity management and data protection technologies help banks exchange funds, people cross borders, energy become smarter and much more.
More than 30,000 organizations already rely on Thales solutions to verify the identities of people and things, grant access to digital services, analyze vast quantities of information and encrypt data.
In early 2019, Thales acquired the international security company, Gemalto and have combined it with its existing digital assets to create a new leader in digital security. Every organization around the world is in the midst of a digital transformation and stands to benefit from their joint innovations.
As the world becomes more connected, Thales makes it more secure.
A big Thank You! to all the DEEP participants
Dear DEEP participants,
We’d like to simply thank you for being there, enabling our first DEEP to happen. According to the initial responses, we might consider it a success and, hopefully, start of a new tradition. Even if it is over, it isn’t! In a few weeks we will open a new section on this website, one where you’ll bee able to hear or read the presentations, as well as look at the photos and videos from the conference. In the meantime, we are available for your questions and requests at all the usual means of contact.
Kind regards,
DEEP team